Monitor your IT security policies
Detect whether assets meet the security standards expected by your organization and other external compliance needs, flagging the assets that need attention.
Monitor IT asset security compliance
Get a thorough, up-to-date picture of which of your assets may be vulnerable to exploits. Ensure that detection and response capabilities provide coverage across the enterprise.
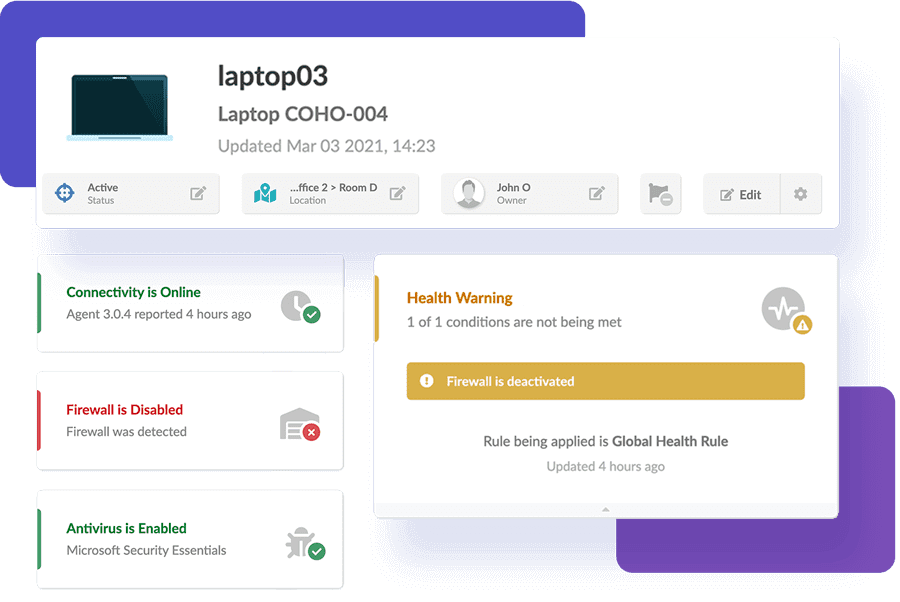
Strengthen Asset Governance with Chain of Custody
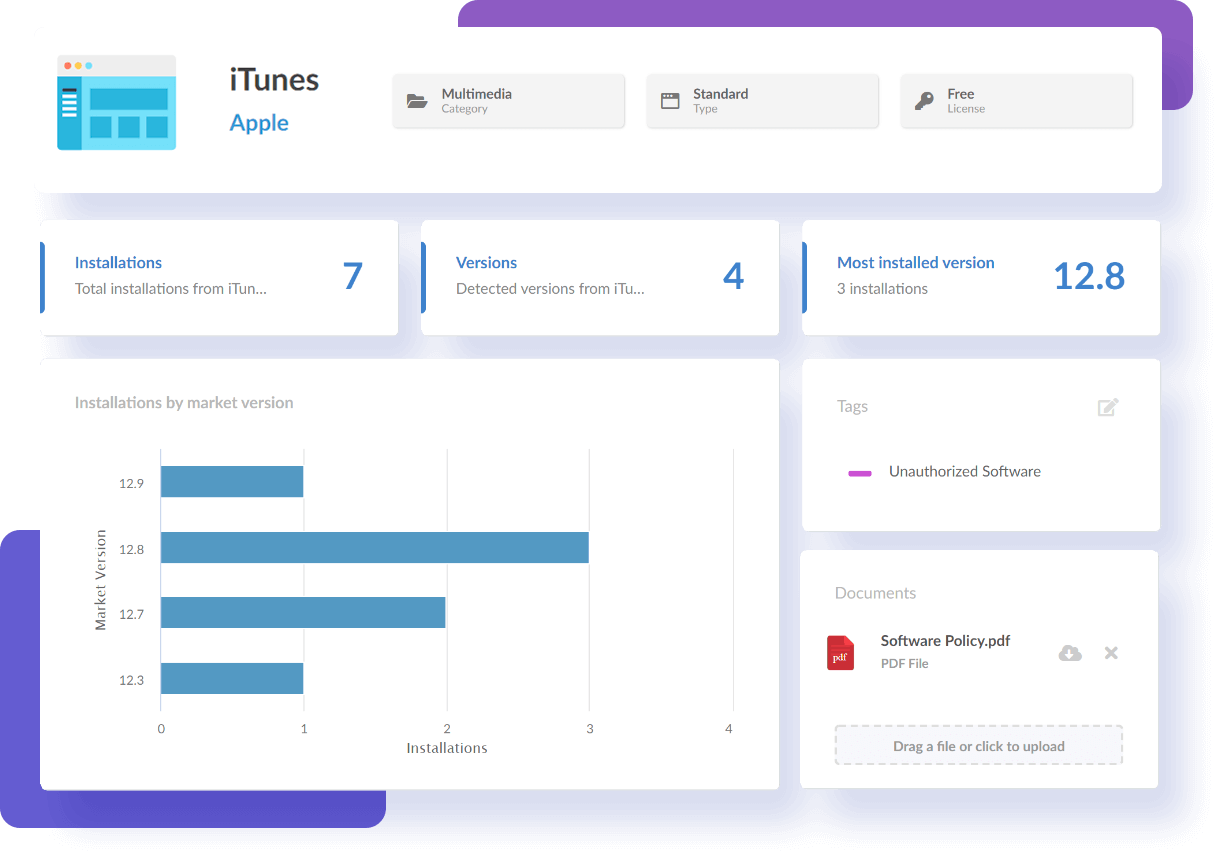
Detect devices running unauthorized software
Prevent and detect unauthorized software from accessing your network by keeping track of which client devices are running unauthorized software, as well as detecting changes to your software and configuration parameters.
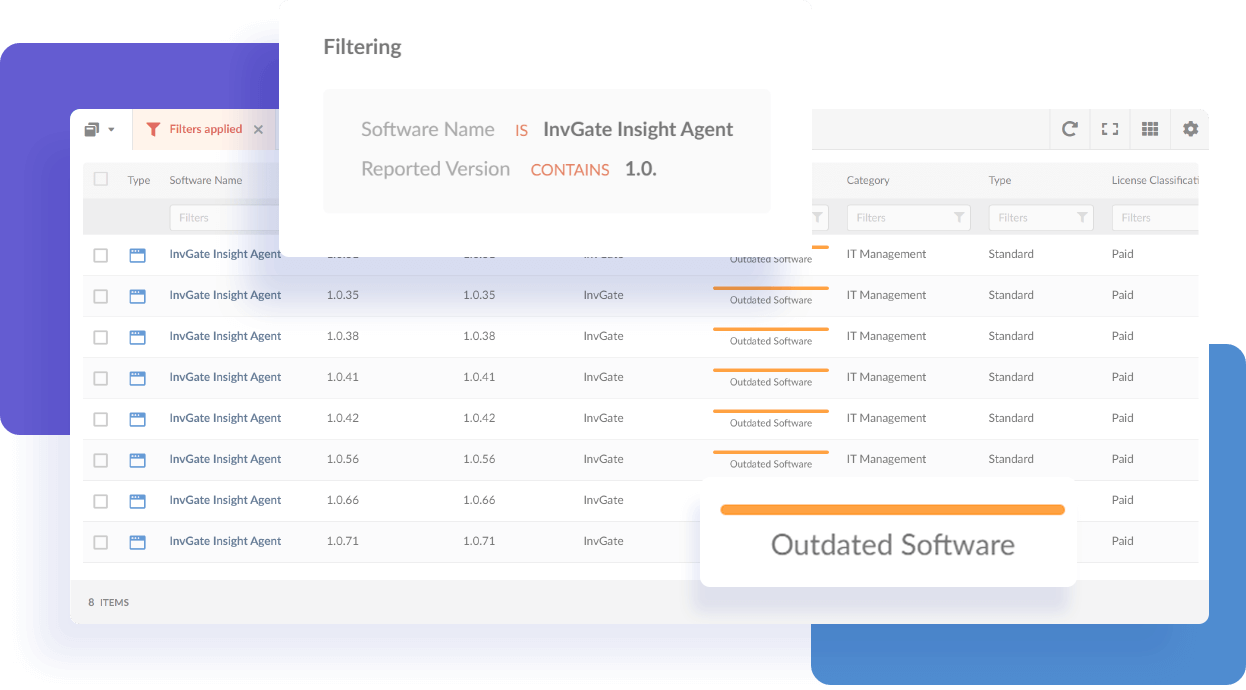
Report outdated software
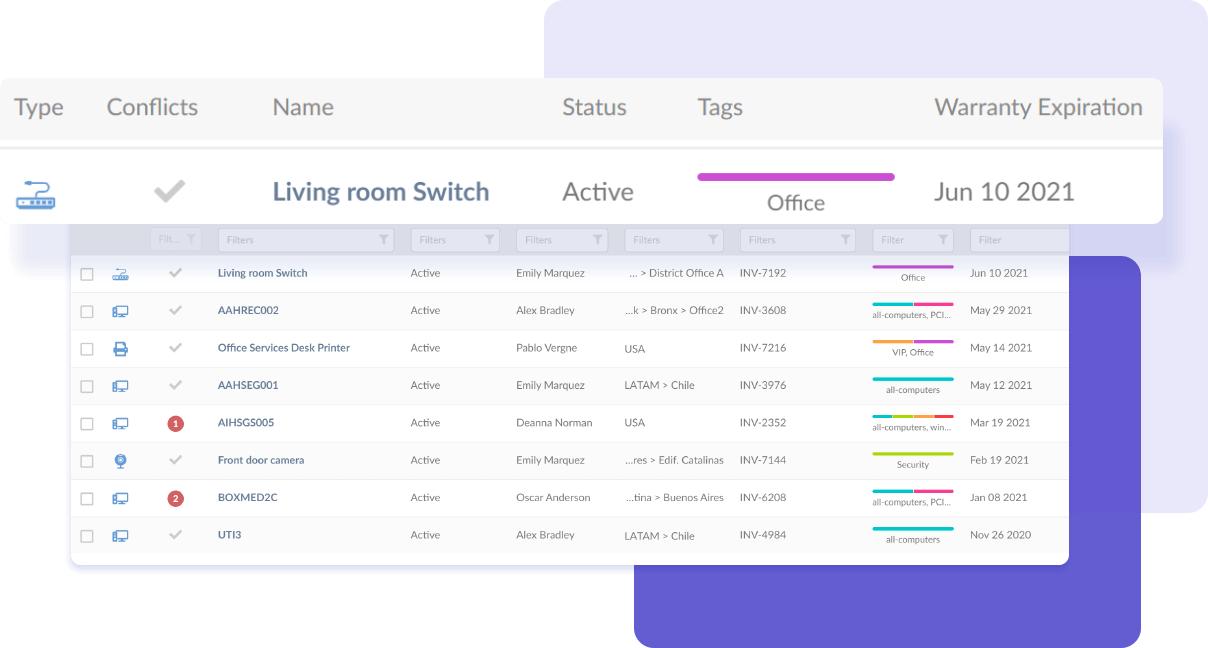
Check assets with expiring warranty
Why is IT Security Compliance Important?
IT security compliance ensures businesses protect digital assets, safeguard customer data, and maintain trust. It helps avoid fines and penalties while promoting safe practices like regular updates and secure usage.
Internal compliance focuses on employee adherence to company security policies. External compliance ensures alignment with industry regulations and standards, enhancing trust, improving data management, and preventing costly violations.
Discover other Asset Management features
Asset Inventory
Track and manage assets
CMDB
Map your IT infrastructure
Software License Management
Optimize license usage
Remote Management
Make secure connections
Software Metering
Optimize software usage
Network Discovery
Make informed decisions
IT Financials
Gain control over budgets
Asset Monitoring
Monitor and control changes
IT Security
Monitor IT security compliance
Software Deployment
Reduce asset waste
Automation
Make your IT asset management easy
Vendor Management
Clear spending visibility
Smart Recommendations
From data to action